The research of face recognition system began in the 1960s. After the 1980s, with the development of computer technology and optical imaging technology, the application stage that really entered the primary stage was in the late 90s, with the technology of the United States, Germany and Japan. Realized as the main.
Face recognition technology is based on human facial features, input facial images or video streams. First, it is judged whether or not there is a human face, and if there is a human face, the position and size of each face and the position information of each main facial organ are further given. Based on this information, the identity features contained in each face are further extracted and compared with known faces to identify the identity of each face.
First, talk about what is face recognition
1. Analysis of the principle of face recognition technology
Face recognition is mainly divided into three processes: face detection, feature extraction and face recognition.
Face detection: Face detection refers to detecting and extracting a face image from an input image. Usually, the haar feature and the Adaboost algorithm are used to train the cascade classifier to classify each block in the image. If a rectangular area passes through the cascade classifier, it is discriminated as a face image.
Feature extraction: Feature extraction refers to the representation of face information by some numbers, which are the features we want to extract.
Common facial features are divided into two categories, one is geometric features and the other is characterized. Geometric features are geometric relationships between facial features such as the eyes, nose, and mouth, such as distance, area, and angle. Since the algorithm utilizes some intuitive features, the amount of computation is small.
However, because its required feature points cannot be precisely selected, its application range is limited. In addition, when the illumination changes, the face has foreign objects obscured, and the facial expression changes, the feature changes greatly. Therefore, this type of algorithm is only suitable for rough recognition of face images and cannot be applied in practice.
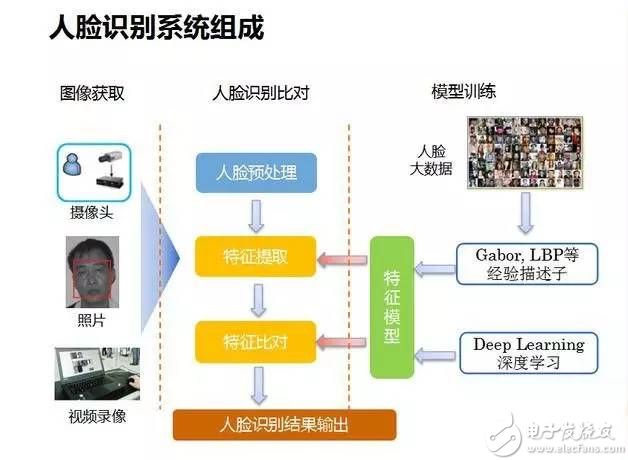
The characterization feature utilizes the gradation information of the face image to extract global or local features through some algorithms. One of the more commonly used feature extraction algorithms is the LBP algorithm. The LBP method first divides the image into several regions, and thresholds the center value in the pixel 640x960 neighborhood of each region, and regards the result as a binary number.
Figure 3 shows an LBP operator. The LBP operator is characterized by a constant monotonic grayscale change. Each region obtains a set of histograms by such operations, and then joins all the histograms to form a large histogram and performs histogram matching calculation for classification.
Face recognition: The face recognition mentioned here is a narrow face recognition, which compares the features extracted by the face to be recognized with the features of the face in the database, and discriminates the classification according to the similarity. Face recognition can be divided into two broad categories: one is confirmation, which is the process of comparing the face image with the existing image of the person in the database, answering whether you are your problem;
The other type is recognition, which is the process of matching the face image with all the images already stored in the database, and answering who you are. Obviously, face recognition is more difficult than face recognition because identification requires a large amount of data matching. Commonly used classifiers include nearest neighbor classifiers, support vector machines, and the like.
Similar to the fingerprint application method, the face recognition technology is relatively mature and is also an attendance machine. Because in the attendance system, the user is actively cooperating, and the qualified face can be obtained in a specific environment. This provides a good input source for face recognition and often results in satisfactory results.
However, in some public places, video surveillance probes, due to light and angle problems, the resulting face images are difficult to compare successfully. This is also one of the problems that must be solved in the future development of face recognition technology.
2. Features of face recognition technology
The human face is as natural as other biological features of the human body (fingerprint, iris, etc.). Its uniqueness and good characteristics that are not easily reproduced provide the necessary premise for identity identification, and face recognition compared with other types of biometrics. Has the following characteristics:
Non-mandatory: the user does not need to cooperate with the face collection device, and the face image can be obtained almost in an unconscious state. Such sampling method is not “mandatoryâ€;
Non-contact: Users can obtain facial images without direct contact with the device;
Concurrency: In the actual application scenario, multiple face sorting, judgment and recognition can be performed;
In addition, it also meets the visual characteristics: the characteristics of “seeing peopleâ€, as well as the features of simple operation, intuitive results and good concealment.
3. Application prospects of face recognition technology
1) Corporate, residential security and management. Such as face recognition access control attendance system, face recognition security door and so on.
2) E-passport and ID card. This may be the largest application in the future. The International Civil Aviation Organization (ICAO) has determined that from 2010, its 118 member countries and regions must use machine readable passports. Face recognition technology is the first recognition mode. Become an international standard.
3) Public security, justice and criminal investigation. Such as the use of face recognition systems and networks, the search for fugitives nationwide.
4) Self-service. For example, if the bank card and password are stolen, the cash dispenser will be taken by others. This can be avoided if face recognition is applied at the same time.
5) Information security. Such as computer login, e-government and e-commerce.
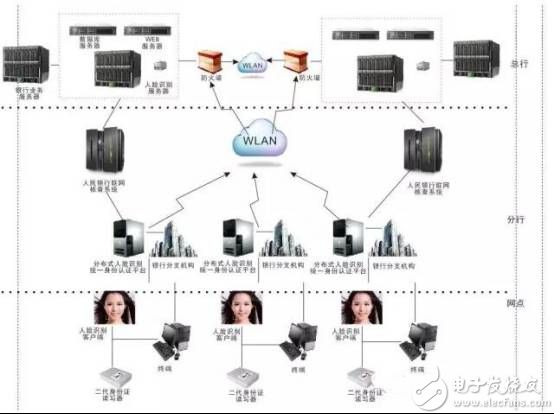
Second, the solution - smart bank face recognition solution
The smart bank face recognition solution is based on the user experience and relies on the intelligent dynamic face recognition verification system, face recognition reward record system, exclusive identity management system, access control management system, video early warning system and other technical support. To create a safer and more convenient smart financial service system.
The smart bank face recognition solution is based on the user experience and relies on the technical support of the intelligent dynamic face recognition verification system, the face recognition reward record system, the exclusive identity management system, the access control management system, and the video early warning system. Create a safer and more convenient smart financial service system.
Realize the counter real name account opening, remote real name account opening, real name payment and other person verification, smart access control, smart attendance, visitor record, VIP identification, financial information advertising precision push and other series of exclusive services to ensure the security of fund transactions, management optimization, business convenience, Attentive service is an important means for banks to broaden their business areas, reshape service processes, improve service quality and enhance market competitiveness.
Solution architecture
Program characteristics
High accuracy, offline work: The world's leading algorithm, completely solve the problem of cross-age issues, small picture recognition, without the need to connect to the public security access documents, can also 100% identification of the authenticity of the documents, whether or not.
Blacklist warning, access control: the first blacklist warning, whitelist automatic identification to open the door, effectively protect the personal safety of customers.
Hierarchical management, face query: Because the collected data is small, the storage has no pressure, and the front-end, terminal, and platform three-level storage are adopted, which facilitates quick query and data backup afterwards. When the secondary business is handled, it can be quickly identified.
Quick recognition, voice prompt: original face recognition algorithm, the fastest 0.2 seconds to determine whether or not, combined with multiple recognition modes to meet the needs of different scenarios. It can be combined with additional voice announcements to make the recognizer easy to operate and pass quickly.
Visible light, multi-person recognition: Based on deep learning, visible light face recognition technology, the environment is not high, to meet a variety of light conditions, in line with human eye habits, and can identify more than 10 people.
System networking, data analysis: mature product system-level application solutions, so that each identification device is a data collection terminal, providing effective data for big data analysis, event warning, and accident prevention.
Third, face recognition technology company
1 Cloud from Technology
2 Defiance Technology
3 Jiadu Technology
4 Shang Tang Technology
5 Keda News
6 Platinum Information
7 Zhongke Aosen
8 Anjie Tiandun Technology
9 Yinchen Technology
10 Junyi Technology
11 Fei Ruisi Technology
13 Science and Technology Information Technology
14 çæ³· Technology (Shanghai)
15 matches for intelligence
16 Wisdom Eye Technology
17 pixel data technology
18 Qingda Weisen Technology
19 Rui is information technology
20 Su Hui Information Technology Lion
21 Zhongzhi Yihua Technology
22 RIO Wind Software Technology
23 Qiansuo Technology
24 Weifu Security
25 Trusted Network Technology
26 Yi Deng Technology
-----------------Foreign company-----------------
1 US Identix Corporation
2 US Bioscrypt Corporation
3 Cognitec Systems, Germany
4 Herta Security, Spain
5 Japan NEC Corporation
6 Japan Softwise Corporation
Guangzhou Chengwen Photoelectric Technology co.,ltd , https://www.cwstagelight.com
