Packing is a very effective way to protect the software kernel. At present, the method of packing shells under Linux system is to directly inherit the shelling theory and method of Windows programs. There are limited extensions on the traditional shelling tools. The shelling tools implemented in the LINUX system are still rare. How to minimize the exposure of kernel information under the Linux system, increase the difficulty of anti-reverse means to improve the difficulty of cracking, and hide the shell protection program well, which are the main problems that are currently overcome.
The existing software packer technology is divided into: embedded, add-on and include depending on the way the shell is loaded. The most classic in embedded is Upx, which supports multiple file types and has advanced compression algorithms. However, this method lacks the anti-dynamic tracking function, and the cracker can use the dynamic tracking debugging method to crack Upx. The following describes the add-on pack (SELF pack): adding a code segment that handles safe operations in the original elf file format, but without built-in decompression, it is easy to leak the position of the shell. The inclusion combines both compression and protection of the shell, but the entry address changes during the shell loading process. Combining the advantages and disadvantages of the above three methods of shelling, the article proposes an improved method of shelling protection in Linux system - shelling and refactoring executable file - SRELF [3]. The improved algorithm combines the shell program with the key parts of the code segment and data segment in the target executable file, and introduces polymorphic deformation technology to make the program exhibit polymorphism and improve the anti-cracking ability of the shell program. Good hides the information about the shell. The experiment proves that the improved method solves the problem that the entry address in the packer is easily changed, and the program of the packer appears in the form of polymorphism, which greatly improves the difficulty of the anti-crack.
1 Packing principle
Packing essentially means attaching a special program to the application and pointing the execution entry of the program to the attached special shell. The shell loading process is shown in Figure 1. First, the shell program needs to get the application programming interface -- the API address. Dynamically load the required API address in the code of the packer using the display link. After the shell program, the data of each block is decrypted according to the definition; if the compression technology is used for the shelling, the decompressing is performed before the decryption, and then the decompressed file is mapped to the specified memory address. After modifying the input table of the original program file, fill in the code address in the HOOK-API table, indirectly obtain the control right of the program, and after the checksum test, jump to the original entry point (OEP) [3].
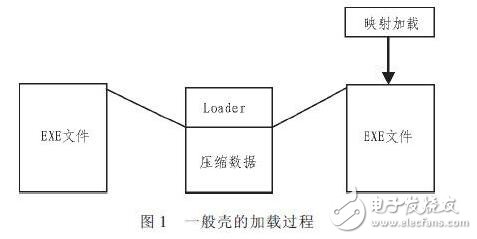
Most of the existing software packer technology methods have changed the original file structure. In the process of relocation, the program's entry address is changed. During the loading process, part of the program is mapped into the address space. If the cracker knows how to add it in one Addressed in the shell program, then the information of the packer can be found when the file is loaded into memory. In response to the above problems, the paper proposes an improved packing method SRELF.
2 SRELF packing method
2.1 Principle of the SRELF method
SRELF—-packing and refactoring executable files, the biggest feature is that the refactoring deformation makes the refactored program polymorphic. First extract the core part of the target elf file, and then combine it with the prepared decryption or decompression program, anti-static analysis and anti-dynamic tracking program, let the packer show polymorphic deformation, and finally traverse the integration program. Reconstruct a new elf executable in the standard format of the elf file.
2.2 SRELF method implementation
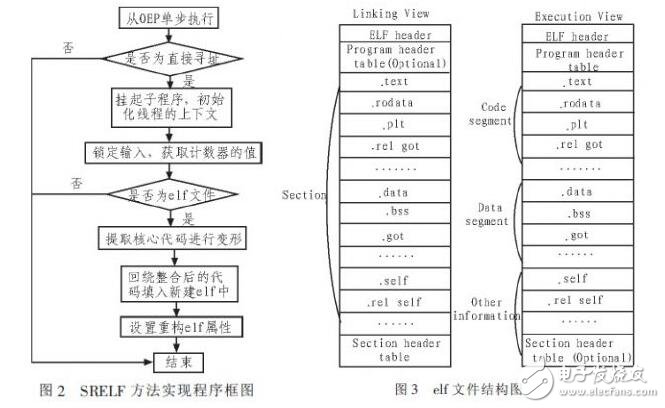
As shown in Figure 2: The basic block diagram of the SRELF packing method implementation. First understand the structure of the application binary interface file (that is, the extension is an elf file). Figure 3 shows the structure of a standard elf file. As you can see from the figure: An ELF header is at the beginning of the file, and the roadmap is saved to describe the organization of the file. This is followed by some segments or some segments (secTIons). The section contains the information needed to run the file, and the information of the object file is saved for linking and relocating.
The first step: extract the core part of the target file
Extract information such as executable instructions, dynamic link tables, segments, or sections of the core. Due to the indirect jump in the assembler, the disassembly generates control flow graph interrupt, which affects the accuracy of extracting the core code. Here, an indirect jump program is introduced.
1) The OEP from the shell run to the original program performs a single-step down-tracking, and after the exception is thrown, the overflow flag is modified;
2) Analyze the type of operand. If it is a direct addressing type, go to 4); otherwise enter 3);
3) Find the defined statement or function entry, set the CREAT_SUSPENDED counter, if the counter is incremented, open the host process as a suspended child process, call GetThreadContext() to get the context of the child process initialization thread;
4) The judged program performs input lock, simulates the execution position and the target indirect jump operation on the sequence of statements, and copies the contents of the acquired register. After using the indirect jump statement to get the information in the elf header file, locate the header table of GetElfCore, then locate the core location of the required code segment and copy the data from it.
Step 2: Encrypt the extracted core code and combine it with polymorphic techniques
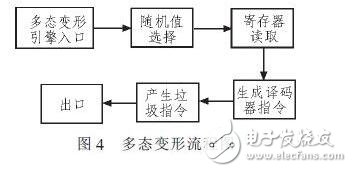
Process injection encryption is used to reversely block the unpacking software from attaching to the protected process. Let CONTEXT.EBX first obtain the PEB address of the child process, read the image address of the PEB child process, point the base address parameter to the retrieved image base address, and finally complete the monitoring of various external interrupts. The encryption of the core code into the polymorphic technology improvement, let it change its own code, so that the search string recognition technology loses its effect. The article uses code transformation encryption compression to hide itself, in order to prevent the search string method from detecting, the decryption code motivates the code module, the program inserts it into itself, calls the function contained in the code module, moves the instructions around the routine, and randomly Adding useless instructions, using different registers and opcodes, makes the binary code corresponding to the decryption routine completely different in different infected bodies. The polymorphic deformation engine process is shown in Figure 4.
Step 3: Integrate the core and packed parts of the target file
The core part and the packed part of the integration target file need to be accurately calculated, and the data of the correct elf file header, program header table, section header table, and the like are set. This will make the newly generated elf file work properly. When integrating data such as elf, the traversal integration method is used to analyze the core code blocks extracted earlier. Use loop rewind to integrate the core code after packing.
1) First set up a status table to record the status type of each variable. Record the size of the physical file and the size of the memory that is loaded into memory. First, the initial state of the function is executed, and all functions except the entry function are set to not. If a variable appears in the status table of multiple forward preamble snippets, recalculate its size and update the status table.
2) Internal execution: Execute its internal instructions one by one in order, change the state table of the variable, continue to write the core part of the target file to the back of the packed part, and form the output status table when executing the last step in the section. At the same time, the security of the deformed state of the program is checked, and the interface function parameters are passed.
3) Loop rewind integration part: When the core code is all executed, check whether there is a loop header containing deformation in the subsequent code segment. If it exists, the code block is the outermost loop header that satisfies the condition. The parameter of the attribute and size in the program header table is set to the new calculated value, and the type status of the variable in the input and output status table is checked. The change, if it exists, restarts the rewind execution until the state table stops updating.
3 related algorithm performance comparison
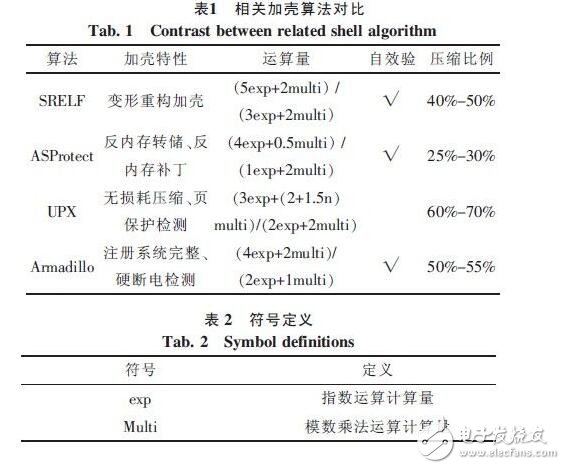
Table 1 shows the comparison of the new packing algorithm SRELF with the ASProtect algorithm, the tElock algorithm, and the Armadillo algorithm. Table 2 gives the relevant symbol definitions.
1) Security improvement
Since SRELF uses binary code for encryption or compression, and does not limit the size of the packed function program, enough flower instructions can be inserted in the code [7]. Coupled with the high complexity of the encryption deformation compression algorithm, the high security of the packer is guaranteed. In addition, the deformation reconstructs the elf file, and the contents of the elf file are all changed. It is more difficult to perform static analysis on the header file. Moreover, sufficient anti-dynamic tracking instructions have been added to SRELF to prevent the protected files from being dynamically tracked. Through the above aspects of security analysis, it can be proved that the security of the elf file after the shelling has been greatly improved.
2) Reduced computational load
3) camouflage enhancement
The structure of the elf file after the shelling has not changed, and the SRELF shelling method does not need to change the program entry address, which hides the shell program very well.
4) scalability improvement
Since the SRELF method does not theoretically limit the size of the shell program, it has a good scalability. Therefore, the encryption method, anti-static analysis method and anti-dynamic tracking method in SRELF can be updated synchronously in the later stage.
In summary, SRELF overcomes the problems exposed in the existing method of packing, and solves the major defects of changing the structure of the elf file and changing the entry address of the program, so that the program after the shelling exhibits polymorphic deformation. The difficulty is added to the shell. Therefore, the SRELF method is a method of packing that has both high safety and good feasibility.
4 Conclusion
In this paper, we study the common problems in the anti-cracking of existing packer software--the emergence of new security flaws that do not meet all known patterns[8], summing up the shortage of shelling methods, and proposing a problem for the shortage. An improved method of packing - reconstructing the deformed SRELF packing algorithm. Software Packing combines key code encryption, deformation, anti-static analysis and anti-dynamic tracking. At the same time, it has a relatively simple calculation amount and improves the anti-cracking ability of the encryption part. In this paper, only the deformability of the program introduced in the process of packing is considered, so that it is not easy to be taken off by the shelling software. The next step will solve the problem of program compression in the process of packing. In addition, the improved method will be further applied to the Linux system software.
aluminium laptop stand amazon,vertical laptop stand india,vertical laptop stand multiple
Shenzhen ChengRong Technology Co.,Ltd. , https://www.laptopstandsupplier.com
