
With the continuous expansion of virtualization technologies such as clouds and containers, east-west traffic in the cloud, data centers, and enterprise networks is showing a rapid growth trend. The collection and analysis of east-west virtual network traffic can help users realize the following values:
Efficient operation and maintenance to ensure business continuity
If the virtual network traffic is not collected, 80% of the user's network traffic will be in a "black box" state. When encountering business delays and interruptions caused by network problems, the operation and maintenance personnel are like blind people. Through the collection and analysis of virtual traffic, the black box can be lighted up, showing a fine virtual network operating state, quickly locating the root cause of the fault, and ensuring the continuity and stability of the business.
Refined operation and increase the input-output ratio
Computing, network, storage, bandwidth, etc. are all resources needed to support services. However, in the current business operation process, there are still problems such as unreclaimed idle virtual machines, uneven network link load, and extensive bandwidth allocation among different ISPs. Through the collection and analysis of virtual traffic, resource usage can be detected in time, resources can be rationally scheduled, resource utilization can be improved, and input-output ratio can be improved.
Safety protection to ensure the safety of the intranet
With the expansion of network scale and flexibility, the internal network security strategy has only increased and changed frequently. However, whether all the currently configured intranet security policies are in effect, and whether the policies that need to be deleted have been cleaned up as the virtual network changes are difficult to answer. At the same time, after the internal network virtual machine is compromised, whether the operation and maintenance personnel can identify the "broiler" in time to ensure the internal network security is a problem that needs to be solved through the collection and analysis of virtual traffic.
Key indicators of virtual network traffic collection
Acquisition performance
As virtual traffic that accounts for 80% of the total cloud data center, achieving full collection requires high-performance collection technology as support. While collecting, other pre-processing tasks such as deduplication, truncation, and desensitization need to be completed for different services, which further increases the performance requirements. Therefore, the collection performance will be a key indicator to measure the virtual network traffic collection technology.
Resource cost
Most virtual traffic collection technologies require computing, storage, and network resources that could be applied to the business. In addition to consuming these resources as little as possible, it is still necessary to consider the overhead of managing the collection technology. Especially when the scale of the node is expanded, if the management cost also shows a linear upward trend, then the collection technology will not have the ideal scalability.
Degree of intrusion
The current common collection technology often requires additional collection strategy configuration on the hypervisor or related components. In addition to the hidden dangers of conflicts with business strategies, these strategies often further increase the burden on the hypervisor or other business components and affect the service SLA.
Deployment dependency
When it is necessary to deploy agents on the hypervisor to implement traffic collection, it is often necessary to consider the dependency conditions for different hypervisor environments, as well as the installation and upgrade of various third-party libraries. In this process, there are often conflicts or incompatibility, which affect the existing production system and increase the difficulty of collection and deployment.
Comparison of existing virtual network acquisition technologies
Strategy Collection
After the control node receives the user instruction, it issues a collection strategy to the virtual network element (usually a virtual switch), and forwards the traffic to the analysis node through a tunnel or other forms to complete virtual traffic collection. Generally seen in SDN network environment.

Pros
• Centralized control by the control node, flexible policy delivery
•Fine-grained on-demand collection can be realized according to business needs
• No dependency on hypervisor system
Cons
• Collection strategy may conflict with business strategy
• The number of strategies that need to be issued for full collection is large, and management is difficult
• Increase the pressure of virtual network elements, uncompressed collected traffic, and high bandwidth usage
Network element collection
Virtual network elements (usually virtual switches) directly provide virtual traffic mirroring capabilities. Users can realize the ability of collecting virtual traffic by calling the corresponding API. Generally seen in mature commercial overall network solutions. Different from strategy collection, the granularity and flexibility of network element collection are mostly limited by the capabilities of the network element interface API.
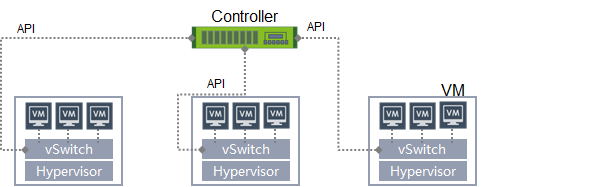
Pros
• Directly call the virtual network element related interface API, easy to implement
•No hidden danger of strategy conflict
• Easy to deploy
Cons
• Limited by the granularity of the interface API, it is impossible to achieve fine-grained control by itself
• Affect the performance of virtual network elements
Agent collection
Run the agent on the hypervisor and start a dedicated virtual machine for traffic analysis. The agent receives instructions from the control node, completes the network configuration, imports the traffic to the traffic analysis virtual machine, and completes the traffic collection. The difference from the strategy collection scheme is that the configuration of virtual network elements is not directly completed by the controller, and the collected traffic does not need to be sent through a tunnel, but directly enters the local virtual machine, reducing network bandwidth usage.
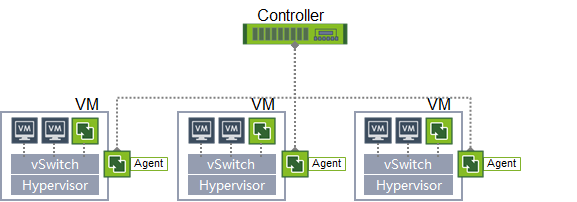
Pros
• The control node does not need to manage a large number of acquisition strategies, reducing the pressure on the control node
•Traffic is forwarded locally to the analysis node (virtual machine) without occupying production network bandwidth
•Can realize fine-grained flow collection
• Deduplication, truncation, and desensitization can be done locally to ensure data security
Cons
• Collection strategy may conflict with business strategy
• Virtual machines occupy part of computing, storage and management resources
•Agent deployment depends on the hypervisor environment
How to realize the next generation of acquisition technology?
The current collection technology has its own advantages and disadvantages. In response to the current ubiquitous virtual network collection needs and pain points, Yunshan Networks launched the patented Trident collection technology to solve the problems of the existing technology and meet the demanding requirements of users for virtual network collection. Trident, as a collection process running independently on the hypervisor, has the following characteristics:

No dependence
Trident is written by the GO language and uses the natural advantages of the GO language to directly generate binary executable program files. The file is only 14MB in size. There is no third-party library or component dependency on the deployment system. Any kernel version greater than 2.2 (released in 1999) Deploy and run on a Linux system.
high performance
Trident uses the "zero copy" technology based on memory mapping to avoid multiple copies of data packets in traditional traffic collection schemes and eliminate the performance bottleneck of network data collection, so as to achieve the smallest resource occupation and meet the huge growth The purpose of network east-west traffic collection. The east-west traffic of all virtual machines on the same host can be collected in full and real-time. At the current 350Kpps acquisition performance, only 15% CPU is used.
Zero interference
Trident can be understood as a "shadow switch", without any additional configuration of existing virtual network elements, it can directly collect all the traffic flowing through the hypervisor, without any interference to existing network strategies.
Fine-grained
Trident receives instructions from the controller through gRPC, can configure ACL filtering rules, cut-off length, desensitization configuration, collection port and other working parameters in real time, or set fine collection strategies for specified virtual interfaces, IP addresses, protocols, and port numbers, and It can be programmed and automated in the control node. It can address the high frequency of virtual machine changes in the virtualized environment and the complex and changeable network environment.
The utility model provides a novel shock-resistant and extrusion-resistant marine pressure gauge. The novel seismic-resistant and extrusion-resistant marine pressure gauge comprises a pressure gauge body and a protective cover, and both sides of the bottom of the pressure gauge body are fixedly connected with installation One side of the mounting plate is provided with a mounting slot, the bottom of the mounting plate is fixedly connected with a box body, one side of the inside of the box body is provided with a drive motor, and one end of the output shaft of the drive motor is fixedly connected with a A turntable, one side of the turntable is fixedly connected with a sliding member, a sliding plate is slidably connected between two sides inside the box body, and a sliding groove is formed on the sliding plate. The novel shock-resistant and extrusion-resistant provided by the utility model This type of marine pressure gauge protects the pressure gauge by setting a protective cover on the pressure gauge to avoid being squeezed or impacted by the outside world during use, causing damage to the pressure gauge, thereby improving the anti-seismic and extrusion resistance of the pressure gauge. Ability.
Pressure Gauge,Water Pressure Gauge,Digital Air Pressure Gauge,Hydraulic Pressure Gauge
Taizhou Jiabo Instrument Technology Co., Ltd. , https://www.jbcbyq.com
