With the rapid development of RFID technology and the continuous reduction of the production cost of RFID electronic tags, the application of RFID tag anti-counterfeiting technology has also been greatly popularized, and it has gradually appeared in various industries, such as transportation, ticketing security, and product anti-counterfeiting. .
Introduction to RFID Technology
The full English name of RFID is Radio Frequency Identification, that is, radio frequency identification technology. RFID radio frequency identification is a non-contact automatic identification technology, which automatically recognizes the target object and obtains related data through radio frequency signals. The identification work does not require manual intervention and can work in various harsh environments.
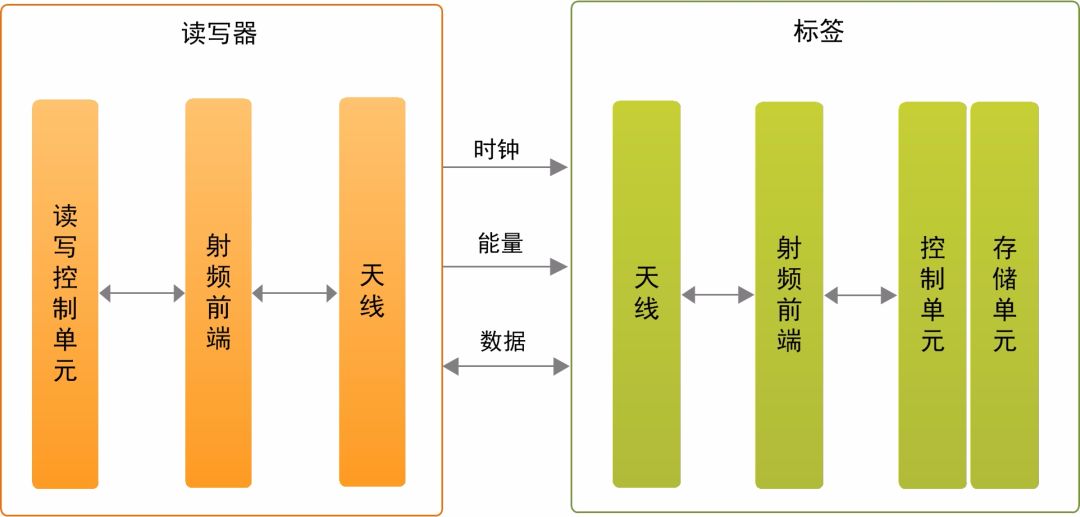
The basic components of radio frequency identification technology include readers, antennas, and RFID tags. Readers are also called readers. They are devices that perform read/write operations on RFID tags. They mainly include antennas, radio frequency front ends, and read-write control units. three parts. Antenna is a device that realizes the spatial propagation of radio frequency signals and establishes wireless communication connections between RFID tags and readers. RFID tags are commonly known as electronic tags, and can be divided into two categories: active (active) and passive (passive) according to their working methods. The internal structure of the RFID tag chip mainly includes four parts: antenna, radio frequency front end, tag control unit and EEPROM storage unit.
The commonly used application frequency classification of RFID can be divided into three categories:
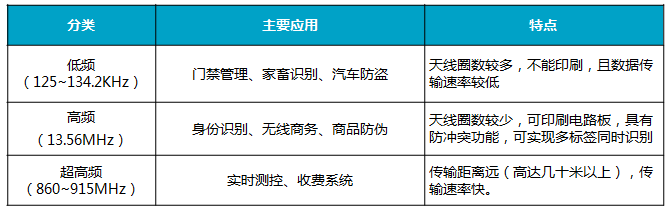
The current RFID tags commonly used for commodity anti-counterfeiting generally belong to the high frequency band (13.56MHz), and follow the ISO-14443A protocol, have an identification distance of up to 10 cm, and have good anti-collision performance and safety performance.
Application of RFID tags in the field of anti-counterfeiting and security
1. Advantages of RFID anti-counterfeiting technology
Radio frequency identification technology (RFID) anti-counterfeiting, compared with other anti-counterfeiting technologies such as laser anti-counterfeiting, special printed symbol anti-counterfeiting, and other technologies, its advantages are: each tag has a globally unique UID number, and it also has an encryption function. Storage space can carry more encrypted information or store data information related to actual applications. No matter from the perspective of security or application flexibility, RFID tag anti-counterfeiting technology has unparalleled advantages.
2. Application examples of RFID anti-counterfeiting technology

Ticket anti-counterfeiting: In public transportation and tourist attractions, fake bill incidents often occur. The use of RFID electronic tag tickets instead of traditional bills not only improves the circulation of personnel, but also plays a role in security and anti-counterfeiting.
Document anti-counterfeiting: internationally, passport anti-counterfeiting, electronic wallets, etc., such as embedding RFID tags on passport covers or documents, such as the promotion and application of second-generation ID cards are typical representatives in this regard. This technology will soon be used in important document issuance management It is widely used.
Commodity anti-counterfeiting: Adding anti-counterfeiting labels in the production and packaging process of commodities is equivalent to providing a reliable way of authenticating commodities and protecting the legitimate rights and interests of commodity producers and consumers. On the other hand, the label itself has a storage function, so in some special applications, the label can also be used to store all the key information during the product life cycle, providing convenience for the subsequent use of the product, not just anti-counterfeiting effect.
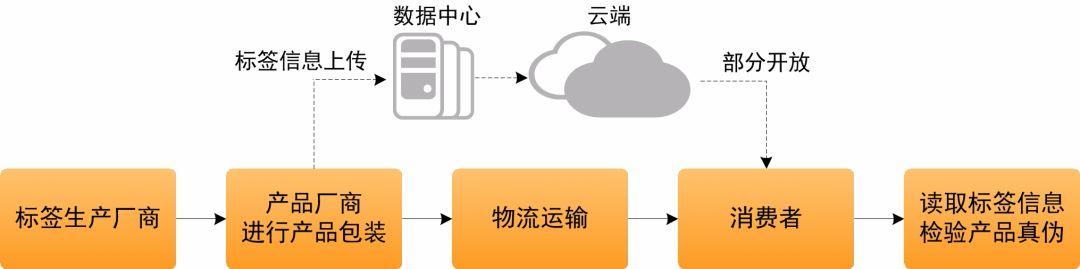
The application of tags in ticketing and document anti-counterfeiting is relatively easy to understand. In the field of commodity anti-counterfeiting, the application process is shown in the figure below. The tag reader/writer used by consumers can be a mobile phone with NFC function.
3. The working principle of RFID tag anti-counterfeiting technology
The main content of the tag anti-counterfeiting technology is to use a reader to read the relevant information in the tag to verify the authenticity of the information. Taking the commonly used electronic tag NTAG as an example, the workflow between the reader and the tag is shown in the figure below. When the reader is close to the tag, the radio frequency field generated by the reader’s antenna transfers energy to the tag to reset it on power. Then the reader follows the ISO-14443A protocol content and activates the tags. This process has an anti-collision function (when there are multiple tags in the RF field, the reader can accurately establish communication with one of the tags).
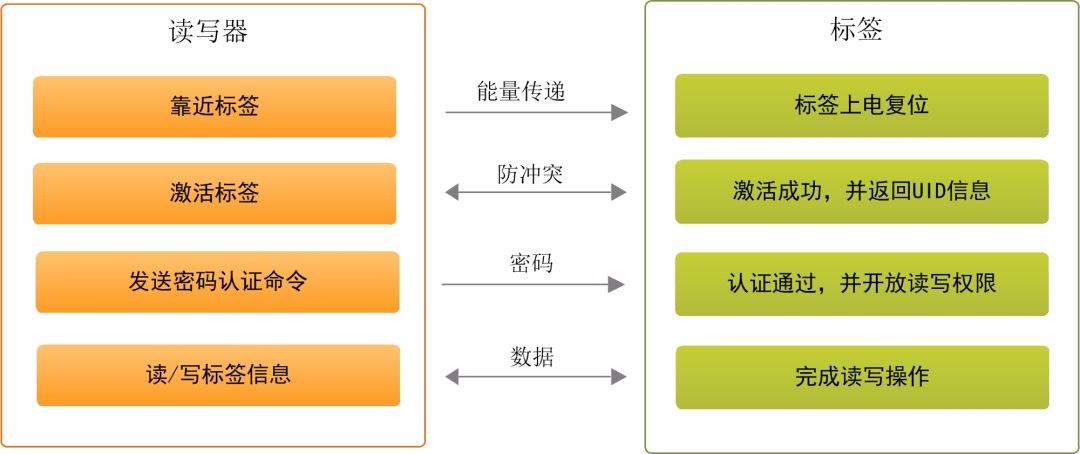
After the tag is activated, password authentication is required for the tag to perform read and write operations. Once the password authentication error or subsequent read and write operations fail, the tag will return to the state after power-on reset, and the tag needs to be reactivated to initiate password authentication again.
Still taking NTAG tags as an example, the actual tag model is FM11NT01. The data interaction during the "anti-counterfeiting verification" process is as shown in the figure below. The password authentication and read-write operation instructions of the NTAG tag start with a specific instruction code, such as the instruction code for password authentication is 1B , Followed by a 4-byte password, and the instruction code of the read command is 30, and the next byte is the starting address of the read operation.
Suppose that the NTAG tag is written with specific product anti-counterfeiting code 23 33 33 33, production date code 20 18 05 20, new password 66 66 66 66 and other information at different positions during the product packaging process. In the product authenticity inspection link, after the label is successfully activated and the password authentication command 1B 66 66 66 66 is received, the 4 bytes 66 of the received password is compared with the internally stored password. If the password is consistent, the read and write permissions will be opened. .
The reader further sends a read command. The command to read address 06 is 30 06. The tag returns 16 bytes from the starting address, that is, 4 pages of data. After obtaining the anti-counterfeiting code of the product, the reader will search for the anti-counterfeiting code in the product information database provided by the product manufacturer, such as query To the corresponding information record, the product is true, otherwise the product is false.
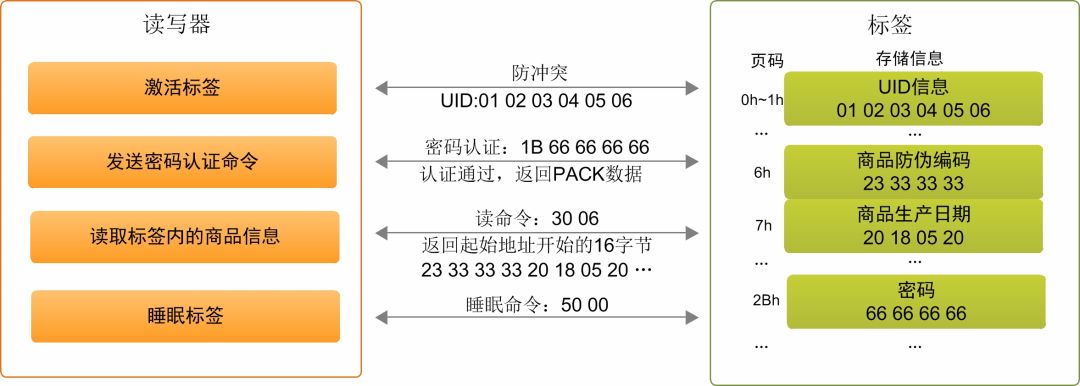
RFID tag anti-counterfeiting application solution
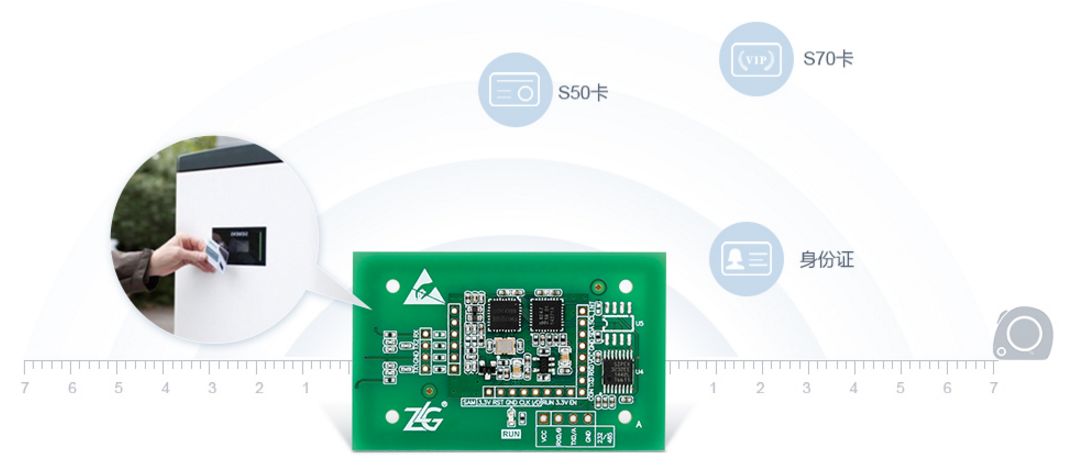
1. ZLG600A series card reader
The ZLG600A series is a 13.56MHz read-write card module based on the Fudan micro-platform. This series of modules complies with ISO14443A/B and ISO7816 standards and supports the operation of Mifare cards, CPU cards and contact SAM cards. Users do not need to understand the underlying registers. A few simple serial commands can realize the RFID card reading and writing function. It has the characteristics of small size, ease of use, and reliability. The physical object is shown as shown, which allows users to conveniently and quickly switch the contact/non-contact Integrated IC card technology into the product.
ZLG600A series card reader modules can not only cooperate with RFID tags to realize various applications in the field of anti-counterfeiting and security, but also have typical application cases in the following fields:
Ticket checking machines for subways, buses, and railway stations;
Various community access control and elevator security systems;
"Three meters" for water and electricity, car charging piles, etc.;
The ZLG600A series card reader module is mainly to meet the requirements of single-point card reading, that is, usually one machine is equipped with one module to complete the product design requirements. Among them, the ZLG600A-DT model supports the expansion of external antennas, and can expand up to two external antennas to meet Part of the requirements of multi-point card reader applications.
2. ARKS16F5xx series card reader core module
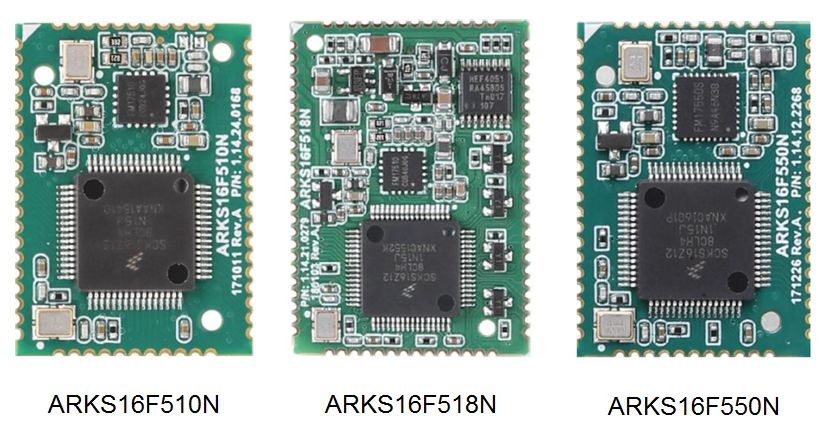
The card reader core module mainly has the following characteristics:
Three specific models are available, fully considering the needs of different customers, with strong application flexibility;
Based on the AMetal software platform, it supports users to carry out rapid secondary development and provides various card reading function interfaces;
The main control adopts KS16Z128 chip, which is rich in available peripheral resources, ultra-high performance, and extremely cost-effective;
Very low power consumption, support low power consumption external card detection function;
The ARKS16F518N model supports multiple antennas (up to 8 antennas) and multi-point card reading.

The ARKS16F518N card reader core module provides an effective solution for the realization of multi-antenna and multi-point card reading. The most typical application at the moment is to add electronic tags to the filter elements of high-end drinking fountains. Since the filter elements of the drinking fountains need to be replaced frequently from time to time, and the working environment of the filter elements is relatively special, it is inconvenient to have direct contact with other components, so RFID tags have become It is the best choice for anti-counterfeiting. The water dispenser judges the authenticity of the filter element by reading the label information, and immediately updates the use information of the filter element to the storage space of the label, and reads the information stored in the label from time to time to better monitor the status of the filter element Function, such as monitoring the use time of the filter element, when the recorded use time value is greater than the preset value, the water dispenser will remind the user to replace the filter element in time. Other similar applications include air purifier filters, printer cartridges, etc.
Jinan Guohua Green Power Equipment Co.,Ltd. , https://www.guohuagenerator.com
