This application note describes the FPGA (Field Programmable Gate Array) and how it protects the system's key functions and intellectual property (IP). This article explores the various ways of IP protection. SHA-1 challenge-response authentication is considered the safest method. This paper presents a cost-effective authentication scheme that protects SRAM-based FPGA design IP. The features of the DS28E01 and DS28CN01 devices are described.
Over the past 20 years, FPGAs (Field Programmable Gate Arrays) have evolved from prototyping tools to flexible solutions for consumer and industrial applications. As FPGA logic complexity rises from thousands of logic gates to millions of logic gates, the device can accommodate more system-critical functions (ie, intellectual property, IP).
Designers can now choose FPGAs to protect configuration data with a variety of techniques—OTP (One Time Programmable) anti-fuse, flash-based reprogrammable memory cells, and reprogrammable, SRAM-based configurable logic cells. Since the configuration data is stored on the FPGA chip and the chip has a mechanism to prevent stored data reading, both anti-fuse and flash-based solutions provide a relatively secure solution. In addition, unless very complex methods such as unpacking, microprobes, voltage contrast electron beam microscopy, and focused ion beam (FIB) detection are used to "eaves" the silicon body and disable the safety mechanism, the data is corrupted. The possibilities are very low (for a brief background on FPGAs, please refer to Appendix A, FPGA Processes and Related Matters).
However, static RAM (SRAM)-based FPGAs have virtually no security measures to protect IP (configuration data) from illegal copying and plagiarism. The reason is that once the data is loaded, it is stored in the SRAM memory unit, and the memory is easily detected to determine its contents. In addition, there is a lack of security mechanisms to protect the configuration data before loading into the chip, which opens the door to various detection measures. Since the bit stream is typically stored in a separate memory chip and read by the FPGA in a powered-on configuration mode, it is possible to traverse the data. Still, you can find some simple ways to protect your data, prevent artificial copying of configuration data, and plagiarize IP.
Vulnerabilities of SRAM-based FPGAs
Since the configuration data bit stream is exposed to the outside during the power-up phase in the two-chip solution (FPGA and configuration memory), and the FPGA cannot distinguish whether the bit stream is "real data" or an illegally obtained replica, the IP contained in the configuration data is not at all protected. This problem can be partially solved by key and bitstream encryption. However, because this method of protection is costly, it can only be used in high-end FPGAs and is not suitable for consumer products.
No protection
SRAM-based FPGA designs are particularly vulnerable to piracy without bitstream encryption. The configuration bitstream can be captured and reprogrammed into the configuration PROM, or simply played back to clone the original design. This allows cloned products to compete with the original product, steal research and development investments, and reduce the market share and benefits of the original manufacturer.
Even without encryption, anti-fuse or flash-based FPGAs are more secure than SRAM-based FPGAs because configuration data is not exposed externally. However, if the FPGA is programmed by the assembly plant, it is possible for the assembly plant to program and sell more devices (more than the authorized number) without any investment in development costs. Such unauthorized devices are difficult to distinguish from authorized devices and can seriously affect company benefits.
One way to improve the security of SRAM-based FPGA designs to some extent is to use a multi-chip package and package the non-volatile memory with the FPGA. However, if someone opens the package, the data interface between the memory and the FPGA will still be exposed externally, and the security of the configuration mode may still be threatened.
There is basically no formal documentation for the structure of the configuration bitstream (ie, the order of the data bits, how they are encoded and identified). Although theoretically feasible, the ambiguity, complexity, and size of the bitstream make reverse engineering very difficult and time consuming. If the reverse engineering is successful, even if only the reverse configuration of the configuration data stream, it is still possible to hack into the set-top box to steal the service or tamper with the power setting of the vehicle, resulting in the responsibility of the original factory.
Design challenges. ..
To prevent a dramatic increase in system cost, designers must continue to use SRAM-based FPGAs without encryption. But they must find ways to protect IP and keep the cost of security measures as low as possible without having a major impact on the production process.
It is important for the design to put the hardware circuitry for security protection into the space allowed by the board without increasing the overall power consumption. Also, the impact of security on FPGA resources (for example, the number of pins and logical units) must be as small as possible.
Response: Certification
The purpose of the authentication process is to establish identity verification between two or more entities. The key-based authentication method calculates the information verification code (MAC) by taking the key and the verified data (ie, "information") as input. The MAC is then appended to the message, and the recipient of the message performs the same calculation and compares its calculated MAC with the MAC transmitted with the message. If the two MACs are the same, the information is judged to be reliable.
This basic model has a disadvantage: the intercepted message can be subsequently resent by the non-authenticating issuer and is mistaken for authentication. If the MAC calculation contains a random challenge selected by the MAC receiver, the probability of success of such a simple "replay attack" will be avoided. Figure 1 shows the general concept of this mode. The longer the challenge code, the more difficult it is to record all possible responses.
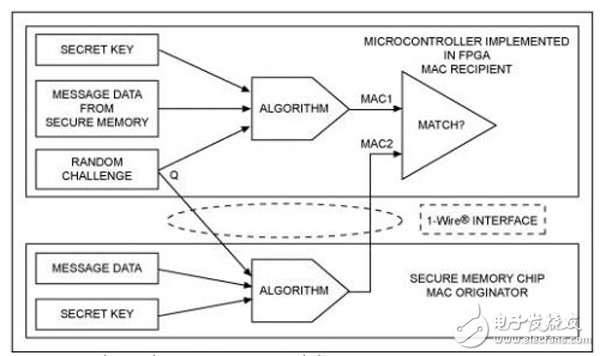
Figure 1. The challenge-response authentication process verifies the authenticity of the MAC sender
15Inch Woofer,15 Inch Woofer,15 Inch Loudspeaker,Carbon Fiber Woofer
Guangzhou BMY Electronic Limited company , https://www.bmy-speakers.com
